Browser profile settings: Fingerprint section
Who can use this feature?
- 👨💻 Account owner, manager, and operator
- 💰 Available on all plans
Fingerprint settings let you dive deep into how your browser profiles behave – things like screen resolution, media devices, graphics data, and more. These settings affect your browser fingerprint and can help you blend in better or customize your profile exactly how you want.
Heads up: we don’t recommend changing these settings unless you really know what you’re doing. Our system already generates safe, optimized defaults to keep your profiles stealthy and working smoothly.
If you’re ready to take full control, switch to the “Fingerprint” section in your profile and explore these expert options carefully. Below, you’ll find an easy guide to what each setting does and how to use it wisely.

Want to understand browser fingerprinting, how it tracks you, and how to avoid account bans in 2025? Check out this in-depth guide on browser fingerprinting, online privacy risks, and how Multilogin’s virtual profiles keep your accounts safe.
WebRTC
WebRTC is a browser plugin used by web apps for speedy direct connections. But since WebRTC uses a UDP protocol, it skips the proxy that's set in your profile. This can allow websites to uncover your actual public, local IP addresses, and media devices, even if you're using a proxy.

Masked
In this mode, the system aligns public and local IPs with your proxy.
Here's how it works: when you launch a profile, it first connects to our server. We detect the actual external IP, feed it back, and establish it as the WebRTC IP. If your proxy IP changes mid-session, we promptly adjust it to keep everything in sync.
Custom
Choose this option to manually set the desired WebRTC IP – it should normally match the IP of your proxy.
Real
In this mode, websites will see your real WebRTC IP. This can be helpful if instead of a proxy you use a VPN or a 4G/5G connection.
Disabled
Websites won't be able to read your WebRTC parameter, as they will see the WebRTC plugin as disabled.
Timezone
Websites can discover your timezone in two ways:
- By running your IP through an IP2Geo database
- By using a JavaScript script that looks at your computer's regional settings through a browser
Then they compare these results. If they don't match, it probably means you're using a proxy server in a different timezone than your computer. In Multilogin, you can ensure these results are consistent using the settings below.

Masked
If you want your profiles's timezone to match your proxy automatically, just stick with the default option “Masked”.
Custom
Choose this option to manually pick the desired timezone from the drop-down list.
Real
If you need websites to see your actual timezone, set it to “Real” – your system timezone will be displayed.
Geolocation
Browsers can allow websites to find your geolocation using an API.
Here's the process: when a website calls this API, the browser prompts you to accept or deny the request and remembers your choice.
Since the location tied to an IP address can change, browsers use a reliable tool to get updated info – Google Maps API. They may send data points like the IP address and available Wi-Fi networks to Google and receive back the coordinates.
Geolocation access
This selector controls the behavior of the pop-up window that asks if you want to share your geolocation.
Sharing it with websites can boost trust. Just a heads-up: a website might grab your geolocation on one page, like maps, and then use it to cross-check with other location clues, such as your IP address, on different pages or even different domains.

Prompt
Whenever a website asks for your location, the browser shows a pop-up window to confirm if you want to disclose this info. From there, you can choose to allow or block access. It's the default set-up in most browsers, keeping you in control.
Allow
Geolocation is automatically shared with any website that requests it.
Blocked
All websites are automatically denied access to your geolocation.
Geolocation data

Masked
In this mode, the system aligns the coordinates with your proxy parameters.
Here's how it works: when you launch a profile, it first connects to our server. We detect the actual external IP and fetch geolocation from an updated IP2Geo database. To add some variation, we include a small random offset. This tweaked geolocation is then shared with websites you authorize. Simple as that!
Custom
Generally, we do not recommend setting up geolocation parameters manually, as this can cause geolocation and IP data mismatch. However, this option can still be beneficial in some cases.
Put your coordinates in the "Latitude" and "Longitude" fields. The "Accuracy" field tell websites how precise those coordinates are, measured in meters.
Browser languages
This property helps websites identify your preferences and adjust their content language, if available.
Browser interface language is the same as your OS language. If you would like to change it, the system language on your computer must be changed first.

Masked
By default, we set the most common property – English.
Custom
You can set your own parameter in two ways:
- Visit browserleaks.com/ip in the preferred browser, copy the Accept-Language value and paste it into the custom field
- Click “Select value”, choose the preferred languages, and adjust the order if needed
For best results, opt for the language that corresponds to your proxy. For example, if your proxy location is Vietnam, select Vietnamese.
Real
Use this option if you need websites to see your real Accept-Language and locale values.
Screen resolution
Analyzing the screen resolution is a common method for browser fingerprinting. These tips will help you avoid red flags:
- Don't use resolutions larger than your native one: websites might check for differences between the declared resolution and the available screen area
- Be consistent in a team: keep profile resolutions within the smallest screen used in your team (if your device is 4K and a colleague has Full HD, set the resolution to 1920 × 1080 or smaller)
- Don't minimize the window: when Multilogin launches a profile, it's maximized according to the resolution in profile settings; it's best not to minimize the profile, since most users have their browsers maximized

Masked
You will get a random screen resolution from our fingerprint builder.
Custom
Set the desired parameter using the tips above.
Real
Websites will see your real screen parameters.
Font data
Font list enumeration
Masked
You will get an optimized list of fonts based on the browser profile's OS.
Real
Websites will see your real font data.
Media devices
WebRTC is a browser plugin that enables audio and video communication on a web page. To make this happen, it taps into your media devices like microphones, cameras, and headphones. But this process can get risky – keep reading to learn why!

Device enumeration
Websites can use WebRTC to check out all your devices, making a list of what you've got. While just this list might not pinpoint you specifically, it can still contribute to creating your digital portrait.
In Multilogin, you can customize the number of different devices within these limits:
- 📷 Video inputs (number of web cameras): 0–1
- 🎤 Audio inputs (number of microphones): 0–4
- 🔊 Audio outputs (number of speakers or headphones): 0–4
Masked
You will get optimized parameters from our fingerprint builder.
Custom
You can select your own set of media devices using the recommendations above.
Real
In this mode, websites will see the real parameters of your media devices. This can be helpful if you want to use a camera or a microphone in your browser profile.
Navigator
The Platform parameter refers to the platform a browser is compiled for. Some platform value examples include Win64, Mac Intel, and Linux 686.
HardwareConcurrency
OSCPU
The OSCPU parameter refers to the version of your operating system. It can be found in Firefox-based browsers (Stealthfox in Multilogin). Some examples include:
- Windows NT 10.0; Win64; x64
- Intel Mac OS X 10.14
- Linux x86_64
WebGL + WebGPU metadata
WebGL and WebGPU metadata is like your browser profile's artistic signature. It reveals details about how your device creates graphics on the web, such as the brand of the graphics tool and its specific model. Websites use this signature to recognize and remember you online.

Masked
You will get optimized WebGL vendor and renderer parameters from our fingerprint builder. Additionally, this mode features WebGPU masking.
Custom
WebGL parameters
Set the desired parameters manually:
- WebGL vendor: a company responsible for creating the graphics technology used in a web browser
- WebGL renderer: graphics hardware of your device, such as the model of the video card
WebGPU parameters
You can set your own Device and Vendor ID values for WebGPU. Here are a few tips:
- Use the real values from the website devicehunt.com
- Use a maximum of 4 symbols: 0-9 and A-F
Pay attention to OS-specific requirements:
- For M-series Mac devices, enter “0” in the “Device ID” field
- Manual setting is not supported for Linux systems
If you leave the fields “Vendor ID” and “Device ID” empty, WebGPU metadata will be set to “Real”.
Real
Websites will see your real WebGL and WebGPU parameters.
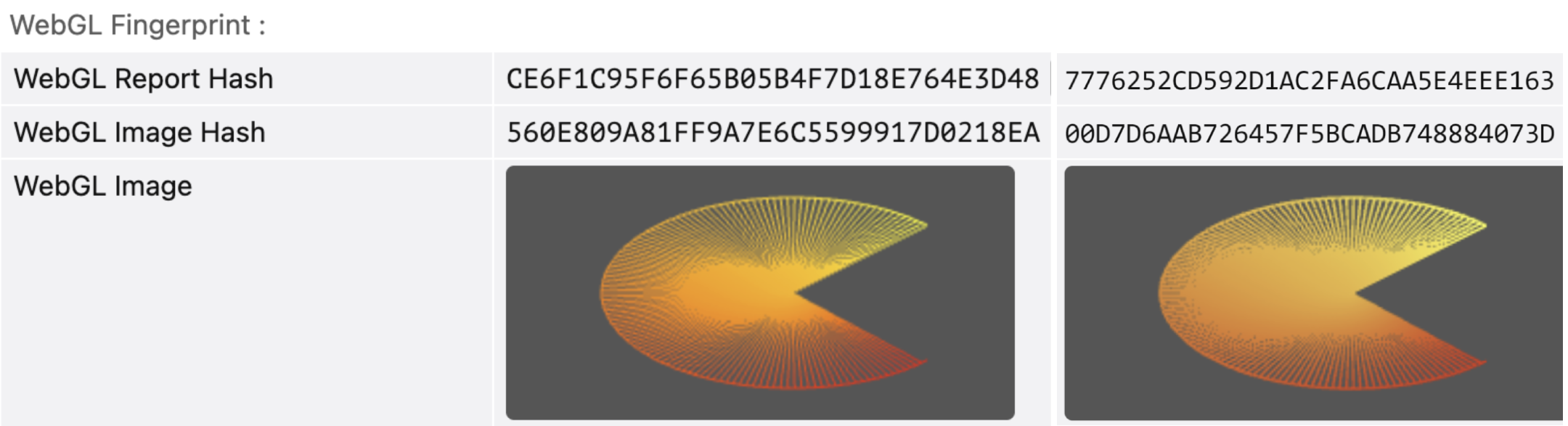
WebGL graphics
WebGL is a JavaScript technology that lets websites create 3D graphics on a webpage. At the same time, websites can use it to identify you in two ways:
- WebGL report: they inspect the entire WebGL browser report table, sometimes turning it into a hash for faster analysis
- WebGL image: they request for a hidden 3D image to be drawn and hashed, as the final result depends on your device's hardware and its calculations

Noise
Real
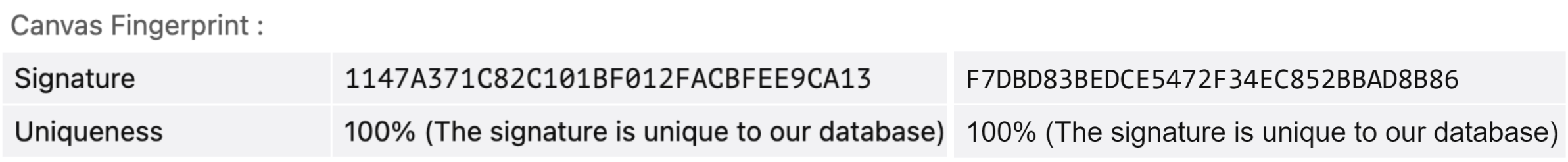
Canvas graphics
The Canvas API is designed for drawing 2D graphics and animations on a webpage via JavaScript and HTML. But just like WebGL, Canvas can add extra uniqueness to your browser fingerprint. According to a study by Princeton University, over 5% of websites use it for fingerprinting.
Here's the process: websites ask your browser to draw a hidden canvas image. This image appears slightly different on various devices, but remains the same for identical setups. Then the image gets transformed into a hash, serving as additional entropy in identification.

Noise
Real
Disabled
Disabling the Canvas API at the browser level prevents websites from reading your canvas fingerprint. However, this is considered a legacy mode and is not recommended for regular use.
AudioContext
AudioContext fingerprint is a hashed derivative of your device's audio setup.
Here's the process: websites ask your browser to simulate a sinusoidal function, mimicking how it plays audio files according to your settings and hardware. This sinusoid is then turned into a hash, which becomes an extra detail in your browser fingerprint.

Real
In this mode, websites will see the real audio fingerprint of your device. It's a recommended choice because many devices generate the same results. Allowing websites to see them helps you blend in with other users who have the same setup.
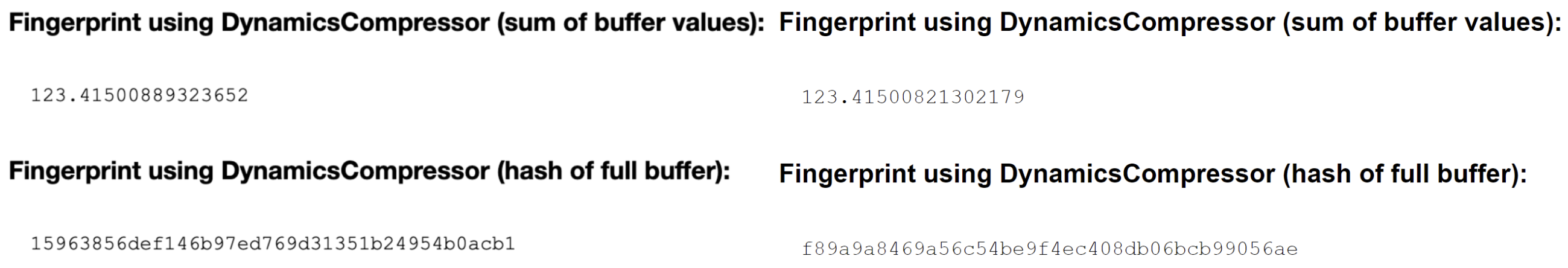
Noise
Multilogin tweaks the audio stack at the browser level, adding persistent noise to make your fingerprint appear 100% unique under statistical analysis.
Key takeaway: even though the noise pattern remains the same, the read-outs will still vary if you launch the same profile on different devices.
Check out the example below to see how the hash changes between two devices.
Port scan protection
When a computer application is active, it opens a port – an endpoint for communication. It can be any number from 0 to 65535. For example, TeamViewer opens ports 80, 443, and 5938.
Certain fingerprint checkers can perform Nmap scanning to check for open ports. Just a heads-up – regular websites don't usually use this due to legal constraints.

Masked
Websites will not see any ports that are actually open in your system. Instead, they will see masked values provided by our fingerprint builder.
Custom
In this mode all ports will be masked except for whitelisted ones. Add such ports to the custom field separated by commas.
Real
Websites will see your real ports.