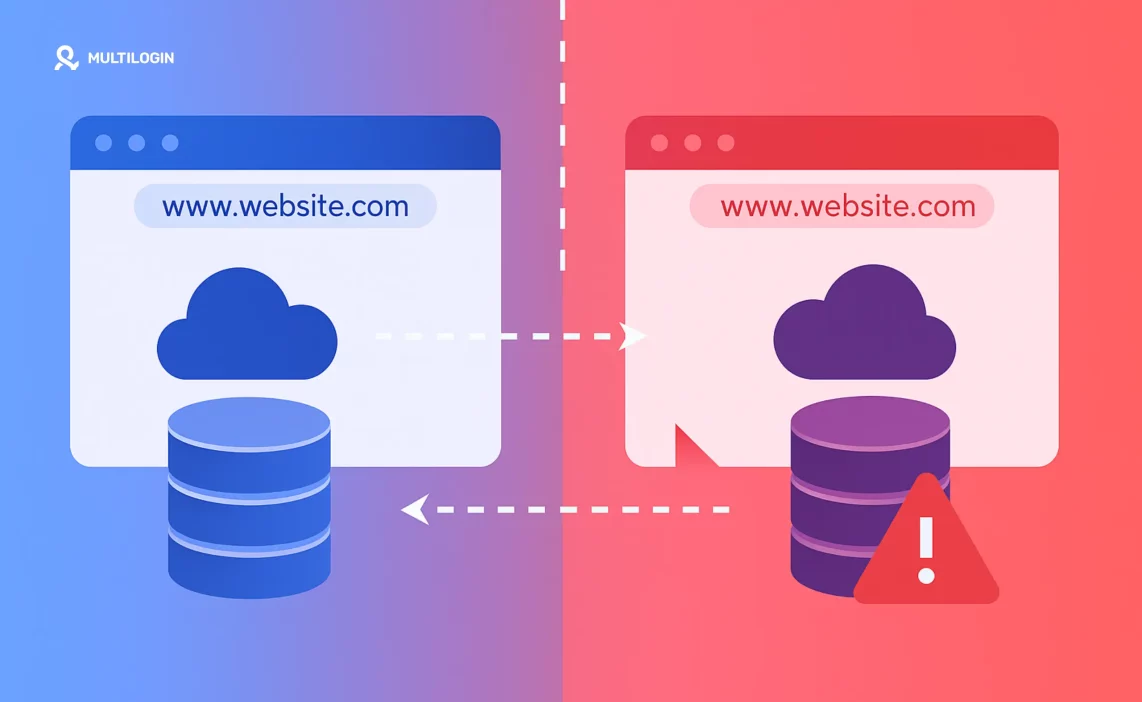
You type in your bank’s website URL — but without realizing it, you land on a fake version. It looks the same. Feels the same. But every keystroke is being logged.
You’ve just been DNS spoofed.
According to cybersecurity reports, DNS spoofing attacks surged by 60% in 2024, targeting both individuals and enterprises. And it’s no longer just a PC problem — Android DNS spoofing attacks are on the rise too.
If you’re wondering:
- “What is a DNS spoofing attack?”
- “How does DNS poisoning work?”
- “Can I fix or prevent it?”
Then this guide is for you.
What Is a DNS Spoofing Attack?
A DNS spoofing attack (also called DNS cache poisoning) is when an attacker corrupts the Domain Name System (DNS) records of a website to redirect users to malicious sites, even if they typed the correct web address.
DNS 101: Quick Refresher
DNS works like the phonebook of the internet — it translates domain names (like bank.com) into IP addresses (123.45.67.89) that computers can understand.
In a spoofing attack, hackers insert false DNS records into the system. So instead of going to the real IP address, your request is sent to a fake server.
The result? You think you’re logging into your bank, but you’re handing your data to a scammer.
What Is DNS Spoofing in Cybersecurity?
In cybersecurity, DNS spoofing is a type of man-in-the-middle (MITM) attack. It exploits the trust between users and DNS servers — and it’s often used in:
- Phishing campaigns
- Malware distribution
- Credential harvesting
- Spyware installation
Because DNS operates quietly in the background, most users don’t realize they’re under attack until damage is done.
What Is a DNS Spoofing Attack on Android?
On Android devices, DNS spoofing can occur in two major ways:
- Through public Wi-Fi networks: Hackers set up rogue Wi-Fi hotspots with manipulated DNS settings, leading your phone to malicious sites.
- Through malware-infected apps: Malicious apps can modify DNS configurations or inject poisoned cache into your device’s network stack.
Symptoms of DNS spoofing on Android:
- Being redirected to wrong websites
Certificate warnings on trusted domains - Unusual popups and site behavior
- Slow or broken website loading
DNS Spoofing vs DNS Poisoning: What’s the Difference?
Great question — they’re often used interchangeably, but there’s a key distinction:
Term | Meaning |
DNS spoofing | The act of faking or forging DNS responses to mislead users |
DNS poisoning | The outcome of DNS spoofing — when the corrupted data is stored in DNS cache |
So:
- Spoofing is the attack method
- Poisoning is the result (corrupt cache)
DNS Poisoning Attack Is Also Called…
- DNS cache poisoning
- DNS spoofing
- Domain hijacking
- Man-in-the-middle DNS attack
Different names, same outcome — you get tricked into trusting a fake site.
How to Prevent DNS Spoofing
Here’s what you (and your business) can do to stay protected:
1. Use DNSSEC (DNS Security Extensions)
DNSSEC adds digital signatures to DNS responses so they can’t be forged. It’s the best defense against DNS spoofing — but adoption is still low.
2. Avoid Public Wi-Fi or Use a Proxy Browser
Free networks = free entry for hackers. Use a secure proxy browser or an anti detect browser like Multilogin to isolate browsing sessions and prevent tampered DNS responses.
3. Update DNS Records Regularly
If you manage domains, make sure to audit your DNS settings frequently to ensure they haven’t been altered.
4. Use Secure DNS Resolvers
Providers like Google DNS (8.8.8.8) or Cloudflare DNS (1.1.1.1) are more resistant to spoofing than default ISP resolvers.
5. Install Anti-Spoofing Tools
Endpoint protection, firewalls, and DNS security monitoring tools can help detect forged DNS responses in real time.
How to Fix DNS Poisoning
If you suspect DNS poisoning on your device or network, do the following:
For Individuals:
- Clear DNS Cache
- On Windows: ipconfig /flushdns
- On macOS: sudo dscacheutil -flushcache; sudo killall -HUP mDNSResponder
- On Android: Switch to Airplane Mode, then back.
- Switch to Secure DNS: Use DNS over HTTPS (DoH) or DNS over TLS (DoT) settings.
- Use a Clean Profile: With tools like Multilogin, you can use isolated browser profiles that don’t inherit DNS poisoning from previous sessions.
For Website Owners:
- Verify DNS records with your registrar
- Enable DNSSEC
- Set short TTL (time-to-live) values to avoid long-term poisoning
DNS Spoofing Detection Techniques
Early detection is critical. Here’s how to spot DNS spoofing:
- DNS monitoring tools (like DNSviz, Splunk)
- SSL/TLS mismatch alerts (when your browser says a certificate is invalid)
- DNS log comparison (check if your DNS records have been changed)
- Behavioral anomalies (users redirected to wrong sites, broken functionality)
Advanced security setups use AI-based detection to flag abnormal DNS behavior instantly.
Pro Tip: Combine DNS Security With Anti-Detect Browsers
Spoofing doesn’t just happen at DNS level — modern tracking systems use browser fingerprinting to lock onto users even after cache resets.
That’s where anti detect browsers come in. Tools like Multilogin spoof both:
- Browser fingerprints
- Session metadata
- And DNS-level identifiers (when used with proxies)
This creates a bulletproof browsing environment — essential for:
- Ad verification
- Multi-accounting
- Global e-commerce
- Cybersecurity testing
Want safer browsing, with anti-DNS fingerprinting protection?
Try Multilogin now for €1.99
Frequently Asked Questions About DNS Spoofing Attack
It’s when hackers fake a DNS response to send you to a fake version of a site — even if you typed the correct address.
Yes — it’s actually getting more advanced, especially with attacks targeting mobile and IoT devices.
Signs include redirects to wrong websites, certificate errors, or phishing-style interfaces mimicking real brands.
Yes — when used with secure proxies and isolated browser profiles, it reduces the risk of DNS-related attacks.
Final Thoughts: DNS Attacks Are Getting Smarter — So Should You
DNS spoofing isn’t just a technical quirk — it’s a real, rising threat that could compromise your data, your business, or your accounts in seconds.
The solution? Secure your DNS path and harden your browser environment with tools like Multilogin.